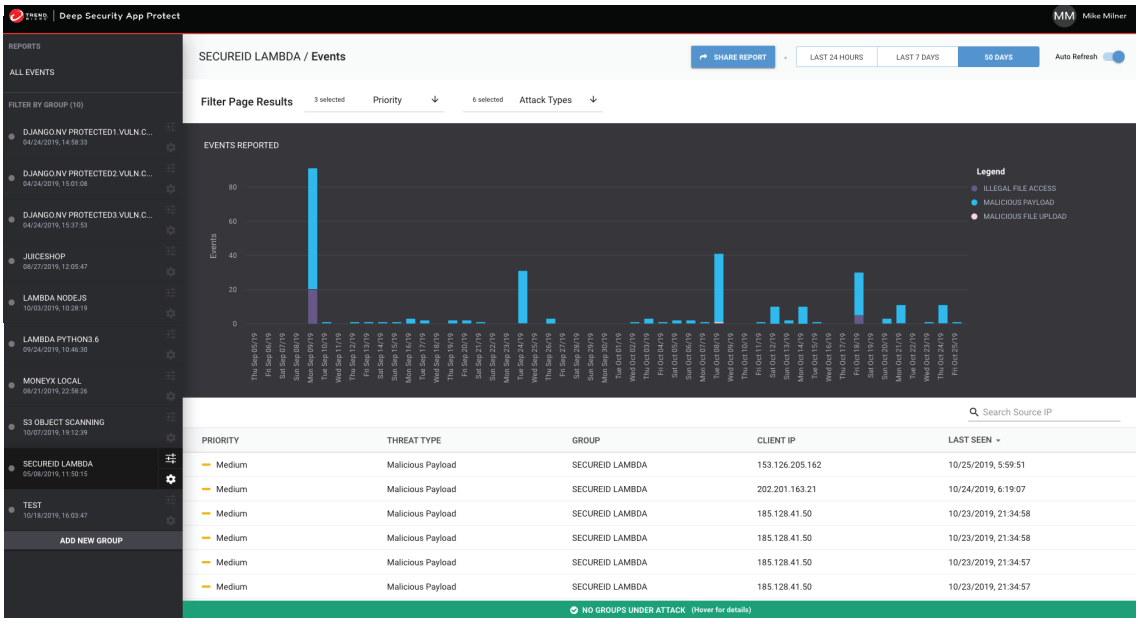
Trend Micro Cloud One – Application Security
Detection and protection for modern applications and APIs built on your container, serverless, and other computing platforms
Overview
Businesses are aligning to cloud-native application architectures faster than ever before. Brought on by streamlined operations processes and the flexibility in build pipeline development tools and services, businesses are using application development as a strategic investment in the hopes that they’ll achieve improved application delivery and customer satisfaction.
A recent study conducted by research firm ESG indicated that 35 percent of businesses were using a combination of containers and serverless platforms for their application builds, with serverless adoption was quickly on the rise.
It continues to become easier to make applications for the web, and businesses are using them at ever-increasing rates. Unfortunately, not everyone—including developers and those who must defend their systems—knows how to secure them properly. With the interconnection of most web applications and IT systems, this lack of knowledge exposes enterprises to security risks from hackers who know how to exploit vulnerabilities in order to gain access to systems, software, and sensitive data.
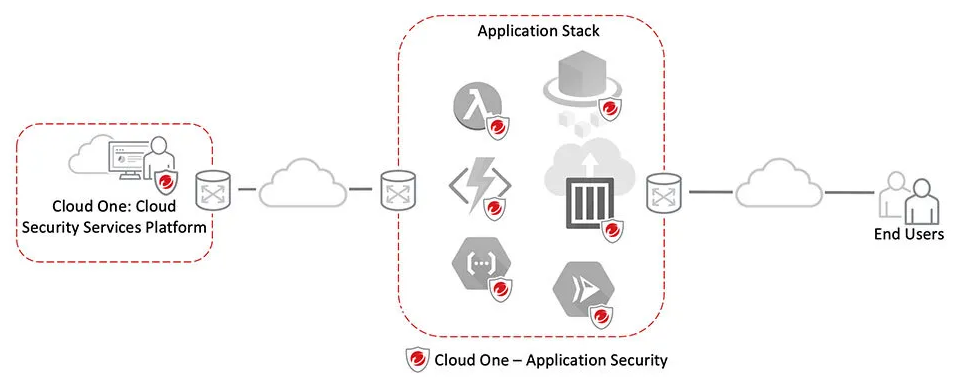
Trend Micro Cloud One – Application Security is built for speedy deployment, with minimal impact on development streams and performance. It only takes a minute to add the library to your application, and there is no need to change your development code. Application Security bootstraps itself into your application at runtime, as opposed to an SDK that has to be integrated into the application. You just need to include the Application Security library with your application and activate it with the application keys. This approach simplifies how security is delivered and is a significant shift for application developers who need immediate, real-time protection for their apps and customers.
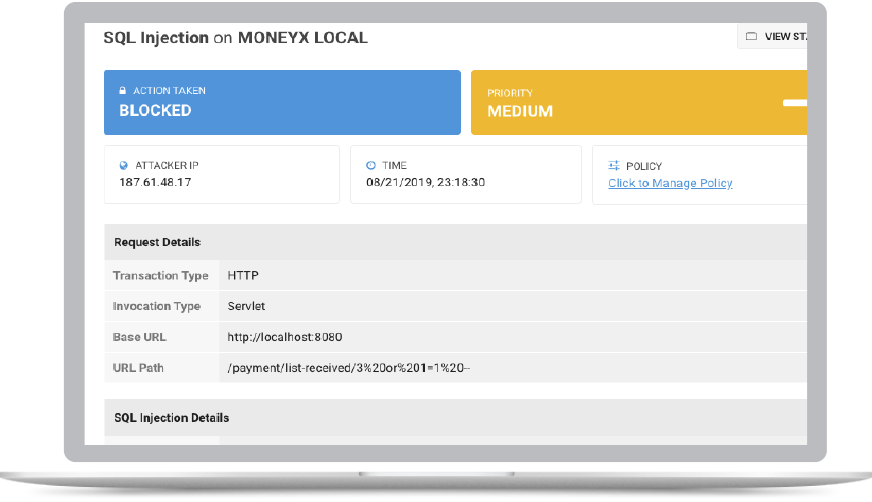
Application Security minimizes design and deployment risks by protecting against sophisticated hacks from inside the application. Optimized for modern application architectures, Application Security immediately blocks unwanted activity in real time to protect data and business logic. The result is unprecedented protection, keeping web application owners and their users safe from hacks with the highest degree of accuracy.
Build secure applications
Protect applications built on dedicated servers, VMs, containers, cloud workloads, and serverless platforms.
Minimize design and deployment risks, and remove the security maintenance burden by protecting against sophisticated hacks from the inside.
Experience faster results
Deploy security as code into applications in only 2 minutes with no additional code changes or rules to set up.
Our more modern, simpler approach to securing your web applications prevents vulnerabilities from being exploited in the first place.
Improve developer productivity
Spend more time delighting your customers with a great application and less time on tedious maintenance caused by coding oversights and weaknesses in dependencies.
Deliver a better experience to your customers, knowing your applications and customer data is secure.
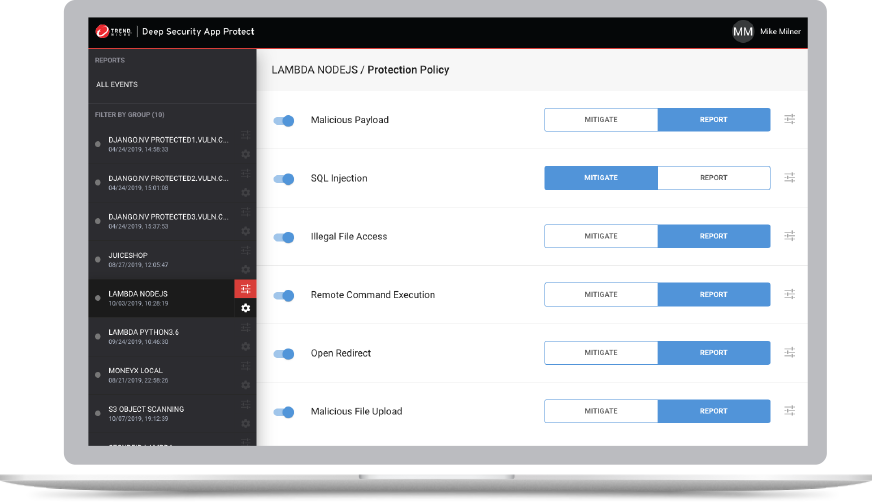
Application Security’s Key Benefits
- Detects and protects against the OWASP Top 10 runtime threats, including SQLi. Remote command execution (RCE) threats are also provided in detection mode.
- Blocks injection and other automated attacks
- Complete coverage and reporting of every attack instance
- Provides full diagnostic details about code vulnerabilities
- Avoids time-wasting false positives and theoretical issues
- Offers insight into an attacker’s identity and attack methodology
- Installs in two minutes—no source code changes required