Trend Micro Managed XDR
Augment your team with expertly managed detection and response (MDR) for email, endpoint, server, cloud workloads, and networks

*Price per User, quantities 251-500
Our Price: $10.93
*Price per User, quantities 1,001-2,000
Our Price: $8.73
*Price per User, quantities 501-1,000
Our Price: $9.61
Click Here for more pricing
Trend Micro XDR- Managed Detection And Response Service
Monitor and correlate more threat vectors
Our threat experts monitor and analyze activity data from the Trend Micro solutions in the environment. Email, endpoint, server, cloud workload, and/or network sources can be correlated, enabling better detections and greater insight into the source and spread of complex targeted attacks.
Superior threat expertise, intelligence, and analytics
Our MDR analysts are skilled and seasoned at interpreting data from our industry-leading solutions. Analysis is optimized by the latest in security analytics and enriched by global threat intelligence. Analysts routinely sweep for threats discovered by Trend Micro Threat Research. This fuels a powerful detection and investigation capability.
Dedicated support for SOC and IT security teams
Our flexible, 24/7 service will alleviate the pain and time for constrained teams to identify, prioritize, and investigate threats. Supplement SOC operations in augmenting detection levels and improving time-to-detect and time-to-respond performance. Maximize effectiveness across multiple security vectors for a single source of detection and response.

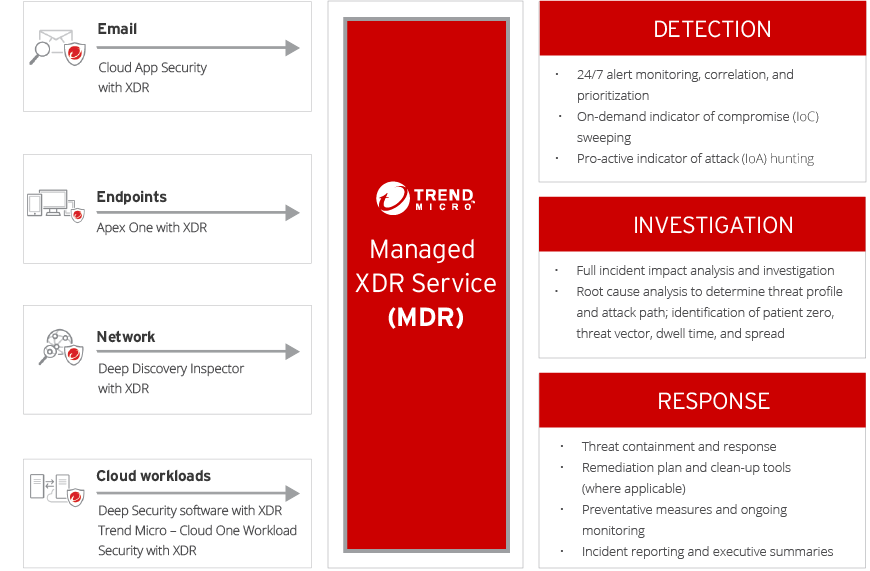
Detection
- 24/7 alert monitoring, correlation, and prioritization using automation and analytics quickly distills alerts down to the events which need further investigation
- Continuously sweeps for newly identified indicators of compromise (IoCs) or indicators of attack (IoAs), including those discovered in other customer environments and shared via US-Cert or other third-party disclosures we receive
- Capitalizes on Trend Micro product differentiators, ensuring customers get the most out of their solution’s detection capabilities
- The MDR service is the first user of any new, cutting-edge detection techniques developed for Trend Micro solutions – you benefit from the latest technologies
Investigation
- Our experts create a full picture of the attack across the entire enterprise – a root cause analysis, attack vector, dwell time, spread, and impact
- Analysts are able to synthesize data into insights, leveraging our global threat researchers with a deep collective understanding of threat techniques and actors
- Customers can work directly with our security analysts during the investigation and response process


Response
- Contains threats and automatically generates IoCs to prevent future attacks
- Provides a step-by-step response action plan to remediate and, as applicable, use custom cleanup tools to help recover from the threat
- Continually sweeps the enterprise to ensure security
- Generates a detailed incident report and regular executive reporting on security posture