Trend Micro Cloud One – Container Security
Continuous protection for your container images and registries, automated within your CI/CD pipeline
Overview
Cloud-first application development strategies are becoming more prevalent amongst companies looking to improve the speed of deployment and cohesive application ecosystems. However, today’s organizations find it hard to manage traditional security solutions with those required by DevOps teams and business units, as they operate with different resources and priorities. On top of that, monolithic approaches to application development are changing how organizations look to transition to cloud, container, and serverless platforms.
The IT analyst and research firm, ESG, recently conducted a survey that indicated 39% of companies are deploying a cloud-first strategy, whereby new applications are only to be built using public cloud services—unless there is a compelling case to deploy on-premises.
With production workloads shifting to cloud-native platforms and DevOps teams adopting security best practices across their build pipelines and cloud-native applications, security solutions need to be designed to succeed across environments (physical, virtual, cloud, containers, and serverless). This provides synergy between IT security and DevOps practices. It also promotes tool consolidation and collaboration of security and compliance requirements, without interfering in continuous implementation/continuous delivery (CI/CD) development cycles.
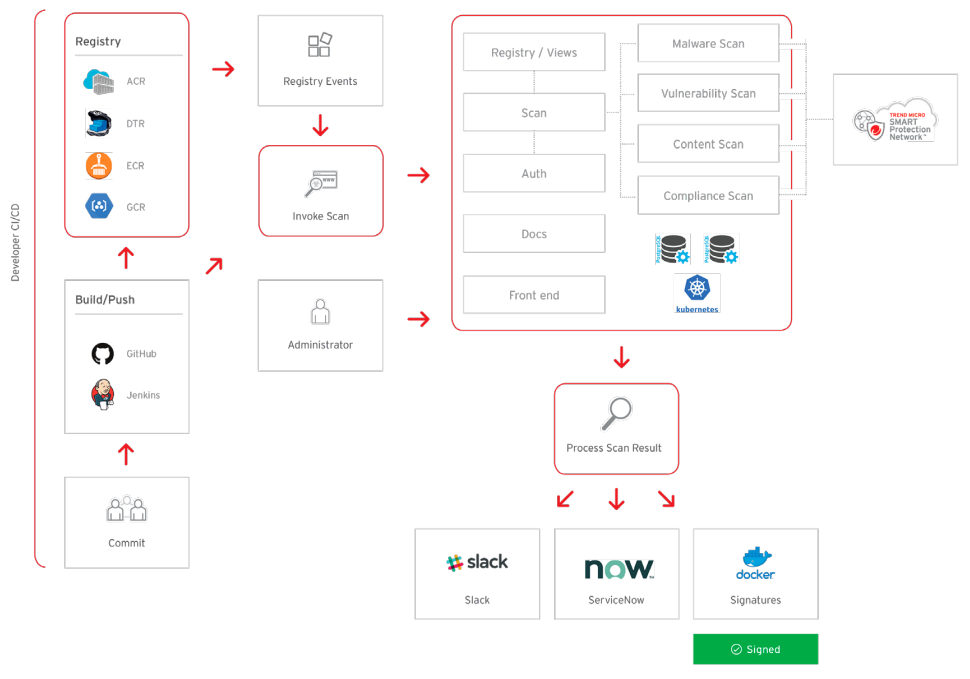
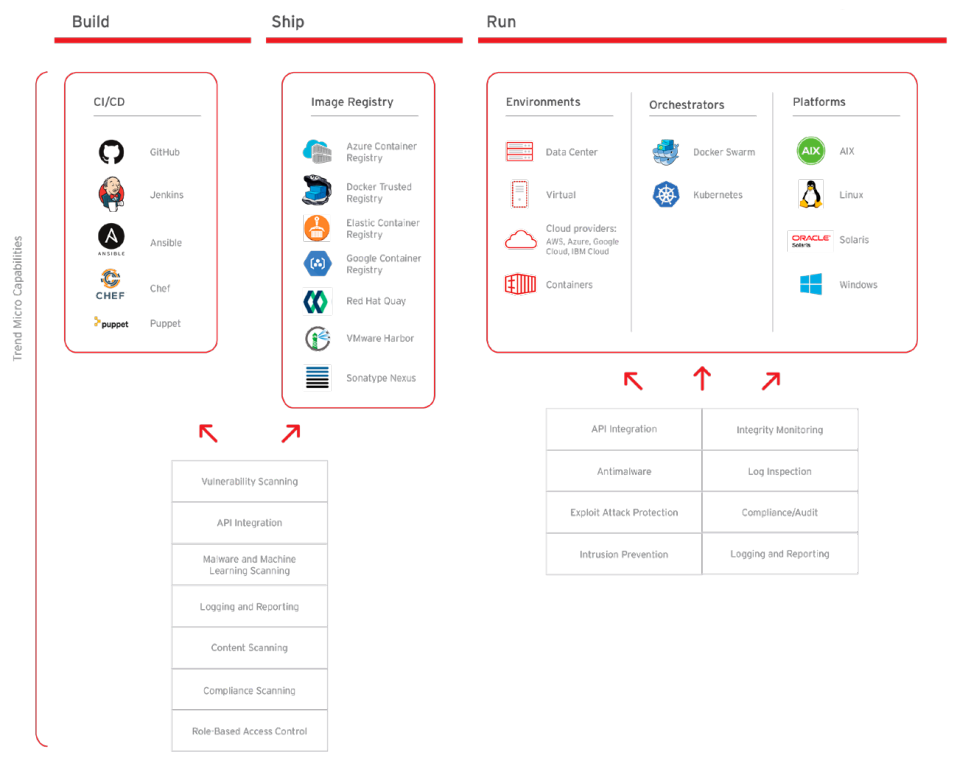
Trend Micro Cloud One – Container Security delivers automated build pipeline container image and registry scanning. Designed for developers and operations teams, Container Security enables earlier and faster detection of malware, secrets/keys, compliance violations, and vulnerabilities, including those found in open-source code dependencies. Additionally, Container Security provides the ability to detect threats in package manager installed apps, as well as direct installed apps, using Trend Micro’s industry-leading rules feed. Container Security helps developers extend even further to the left with Snyk’s opensource vulnerability database, offering early detection and mitigation of vulnerabilities in open-source code dependencies. With Container Security, DevOps teams are enabled to continuously deliver production-ready applications and meet the needs of the business— without impacting build cycles.
Continuous scanning optimized for DevOps
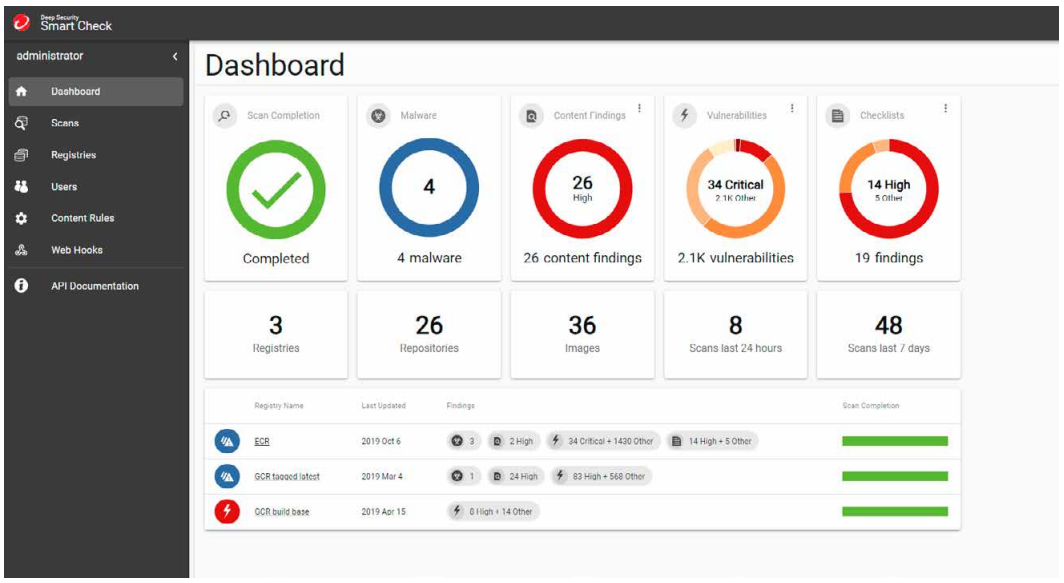
Container Security helps DevOps teams adopt frictionless security with immediate, continuous scanning for threats, vulnerabilities, secrets, and compliance violations. Container Security also provides dashboard visibility, notifications, and scanning logs for compliance assistance. Optimized for leading container platforms, Container Security can be seamlessly integrated into your existing toolchain.
Automate processes with APIs
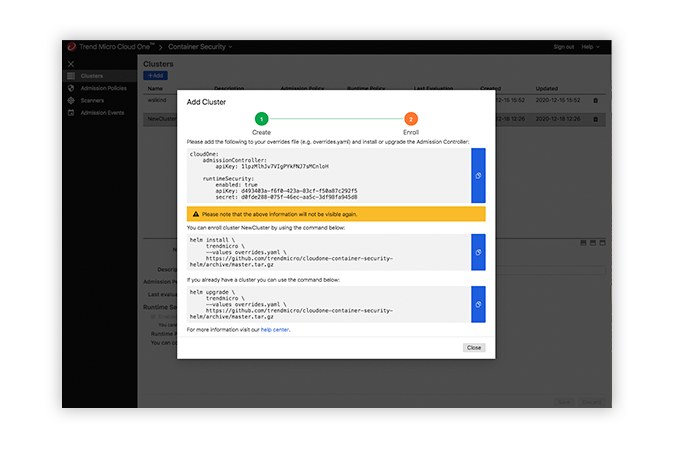
Container Security provides complete automated product functionality using a comprehensive catalog of APIs, purposely built to integrate into your CI/CD pipeline. Container Security allows application architects and developers to bake security as code into their build pipeline for container image and registry scanning. Implementing effective security earlier in the software build pipeline helps to achieve consistent results faster in the development cycle and reduces manual security steps and application downtime.
Smart protection
Container Security reduces disruption of development schedules and workflows with unmatched research and detection of threats, as well as non-intrusive security for the CI/CD pipeline. Container Security eliminates the complexity and volume of threats with detection of vulnerabilities, secrets, and zero-day malware using Trend Micro Smart Protection Network.
Compliance-ready protection
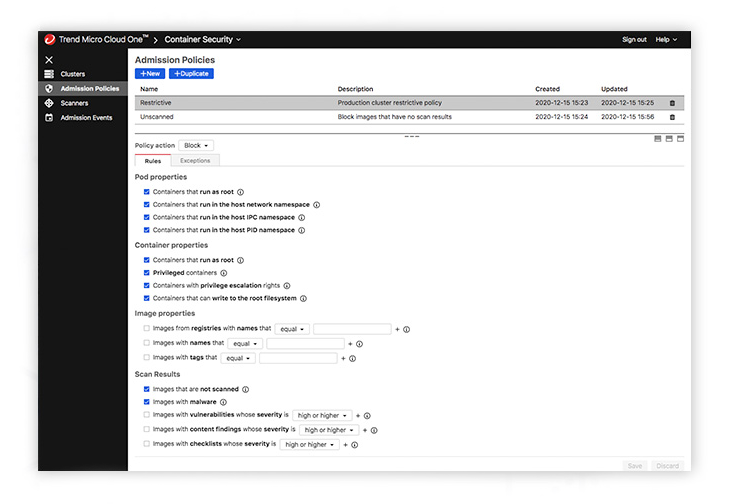
Container Security allows security engineers to meet compliance requirements without impacting productivity and interfering in the CI/CD pipeline. What’s more, it delivers policy compliance scanning, with customizable policies to meet compliance and governance needs. Container Security also offers detailed log history, allowing for easy reporting and auditing.
Key Advantages
- Prevent exploits prior to runtime
Protect against malware, vulnerabilities, and secrets with buildtime and registry scanning of container images. Ensure threats are detected before applications are deployed. - Protection optimized for DevOps
Implement frictionless security early in the CI/CD workflow with security as code and automated protection that won’t slow down your DevOps processes. - Full life cycle container protection
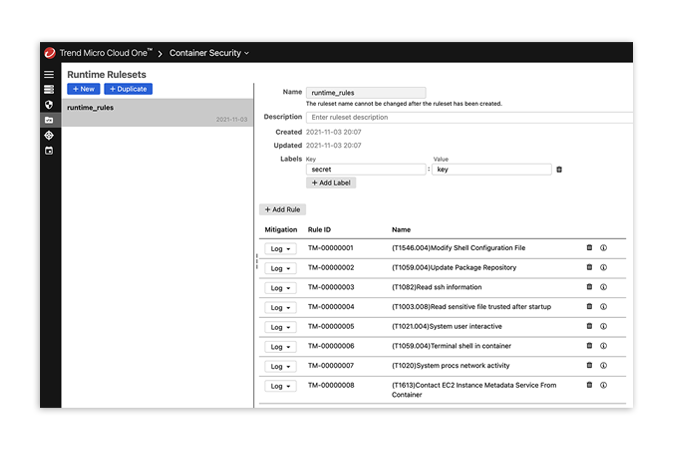
Trend Micro Cloud One – Workload Security complements Container Security, providing leading runtime container protection for full life cycle security of you container.
Complete Cloud-Native Application Security
Security teams can be assured that protection and enforcement are applied to container builds, deployments, and runtime workflows.
Provides security for Kubernetes®-deployed containers, all from one unified solution
Reduces disruption of development schedules with unmatched research, automated detection of threats, and non-intrusive security for the CI/CD pipeline
Designed for modern cloud-native application development and mitigates the risk associated with rapid deployments of microservices
Ensures protection and enforcement are applied to container builds, deployments, and runtime workflows