
Trend Micro Mobile Network Security
Hybrid cybersecurity for enterprise private mobile networks
Advancements in connectivity bring new possibilities. It is essential to prepare for cyber threats that stem from utilizing connected mission-critical applications in a borderless internet of things (IoT) network environment.
Trend Micro Mobile Network Security (TMMNS) is a hybrid cybersecurity solution developed for enterprise customers to ensure the security of mobile user equipment (UE) and IoT endpoint devices, as well as critical edge computing application servers that reside inside of the enterprise’s campus network. Based on the European Telecommunication Standards Institute (ETSI) Network Functions Virtualization (NFV) framework, TMMNS provides a fully virtualized solution that has the flexibility and agility to be deployed in the most popular commercial and open source virtualization platforms with high performance and low latency. Unlike most traditional cybersecurity solutions, TMMNS bridges the gap between information and communication technologies (IT/CT) to provide comprehensive protections, covering the network and endpoint layers to help customers face the new and diverse threats being seen throughout cyberattacks in 4G/LTE, NB-IoT, and the 5G network.
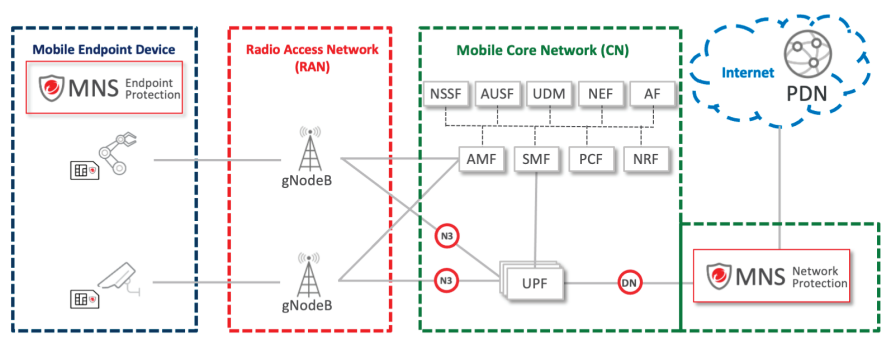
TMMNS in a mobile network
Achieve end-to-end security
Unlike most traditional cybersecurity solutions, Trend Micro Mobile Network Security (TMMNS) provides comprehensive protection by bridging the gap between information and communication technologies (IT/CT). With the network and endpoint layers covered, you can face the emerging, diverse threats targeting 4G/LTE, NB-IoT, and the new 5G network.
Reduce security management workload
Lighten the workload of IT security admins in the enterprise information and communication technology (ICT) with seamless CT/ IT integration and policy management based on IMEI (international mobile equipment identity) or IMSI (international mobile subscriber identity), not IP address. Gain visibility of the risk status of each cellular UE and a simple yet efficient security management in a single console.
Increase cost efficiency
Purpose-built for seamless CT and IT integration, TMMNS is easy to deploy cost efficiently. Its endpoint protection is agentless – no firmware integration required for each cellular UE – and its management modules and network protection have flexibility and agility to be deployed on the most popular commercial, open-source virtualization platforms with high performance and low latency.
Joint-defense Between Network and Endpoint
As a comprehensive solution, TMMNS offers two-layers of protection for your private mobile network:
- TMMNS Network Protection Identifies and blocks vulnerability exploitation, malicious content, and suspicious network behaviors at the data network of a mobile network core, protecting your private mobile network at the network level
- TMMNS Endpoint Protection Provides cellular UE visibility, identifies illegitimate cellular UE, and denies a cellular UE access to its radio access network, protecting your private mobile network at the endpoint level
TMMNS Network Protection and TMMNS Endpoint Protection provide multi-layered protections by performing their functions in individually while simultaneously working together to provide a join defense against cyber threats.
Benefits
Meet end-to-end security in mission-critical private mobile networks
- Ensures that your mobile UE, IoT endpoint devices, and application servers on your MEC system are well protected
- Prevents misused or illegitimate UEs from attacking your IT or OT networks
- Offers you an additional security protection layer across CT/endpoint and IT/network
- Blocks risky cellular UE access to its radio access network, ensuring your private mobile data network is clean
Reduce security management workload of IT sec admin in enterprise ICT
- Purpose-built for seamless CT and IT integration without third-party systems; security policy management is based on IMEI/IMSI rather than on IP address
- Visibility of risk status for each cellular UE
- Simple yet efficient security management in one console
Cost efficiency for deployment in mission-critical private mobile networks
- No third-party systems needed for CT and IT integration, making deployment cost-efficient
- Agentless and no firmware integration required for each cellular UE
Endpoint protection
If an unauthorized device attempts to access the radio access network, TMMNS Endpoint Protection will identify the anomaly behavior and deny access.
Delivered by secure Java applet software, TMMNS Endpoint Protection is deployable on any subscriber identity module (SIM) – physical SIMs, eSIMs, and iSIMs – allowing you to harden mobile UE/IoT endpoint device security in a mobile network environment.
Identity binding continuously monitors and allows access only to registered combinations of UEs and SIMs, adding another layer of zero trust security against attackers who use stolen cards or employees who install corporate cards on risky devices.
Network protection
TMMNS Network Protection identifies vulnerabilities, malicious content, and suspicious network behaviors, blocking them in the wire to protect cellular UE/IoT endpoint devices. Complete identity information of the risky UE is logged for investigation.
- Protects app servers on MEC
- Prevents outbreak attacks from compromised UEs to connected network segments
- Stops compromised UEs from accessing C2 servers
- Shields vulnerable UEs from exploitation
- Prevents malicious UEs from attacking other devices
- Blocks flooding and port scan attacks
- Delivers application identification and URL filtering and control at the UEs
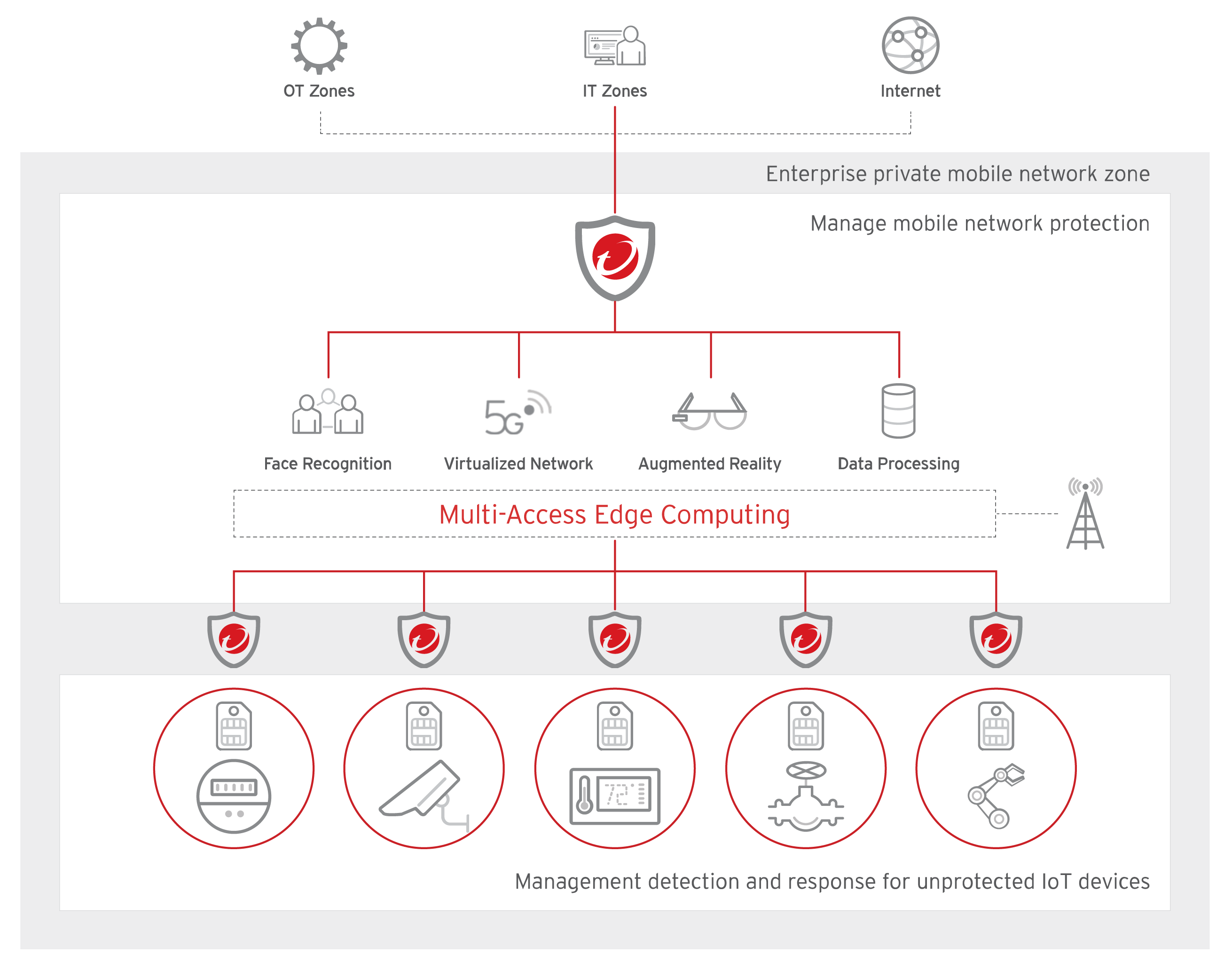
One-stop joint defense between the endpoint and the network
The powerful TMMNS Network Protection and TMMNS Endpoint Protection work together to deliver a TMMNS joint defense, facilitating security operations between CT and IT technology. You have an additional security protection layer across CT/endpoint and IT/network, ensuring a safe mobile data network.
- No third-party system required
- No need to integrate with mobile network components
- Easy and fast deployment
- Reduced security management workload
- Quarantines malicious UEs and blocks risky UE's access to its mobile core data network
- Automatically pauses/stops risky UE’s radio network access by user-defined policies
Protection across multiple industries
Our solutions help system integrators leverage shared band or unlicensed band radio to help build customers’ private mobile networks.

Shopping Mall

Smart Factory

Port

Airport

Mining

Enterprise
