Overview
We call on security products and services to keep our businesses and organizations safe. Most of the time they do exactly what we want them to do; detect, alert, and block threats trying to land a successful attack. However, the downside is that they produce a lot of data, some of it relevant, some of it not. It is up to the security professional(s) in the organization to comb through the potential thousands of alerts or events each day to determine what is actually a threat and decide whether or not they need to respond. Compounding this problem is a worldwide shortage of cybersecurity staff or personnel that needs to be trained to decipher these events.
Trend Micro XDR for Networks (formerly Trend Micro Deep Discovery Network Analytics) automates the correlation of advanced threat events. This provides faster resolution with fewer people involved, while providing an in-depth picture of the full attack. In some cases, you may believe the attack started today, but in fact, the initial breach happened weeks or months ago.
- Continuously analyzes current and historical network metadata and correlates these related threat events into a single view for full visibility of the attack cycle.
- Uses advanced and sophisticated machine learning techniques to detect network traffic anomalies.
- Correlates the events and maps out every step of the attack, quickly answering the questions of of “what”, “who”, and “where”. Giving you a better idea of how to respond and prevent future attacks.
- Combines with other Trend Micro products for correlated detection and integrated investigation and response across email, endpoints, servers, cloud workloads, and networks.
Attack Visibility
- Correlate six months of events
- See the full attack lifecycle
- Go beyond the infection point
- Watch the attack play back
- Learn the methods used in the attack
Prioritization of Response
- Understand the scope of the attack
- Know the attack severity
- Gain quick detection and analysis of comprehensive attacks
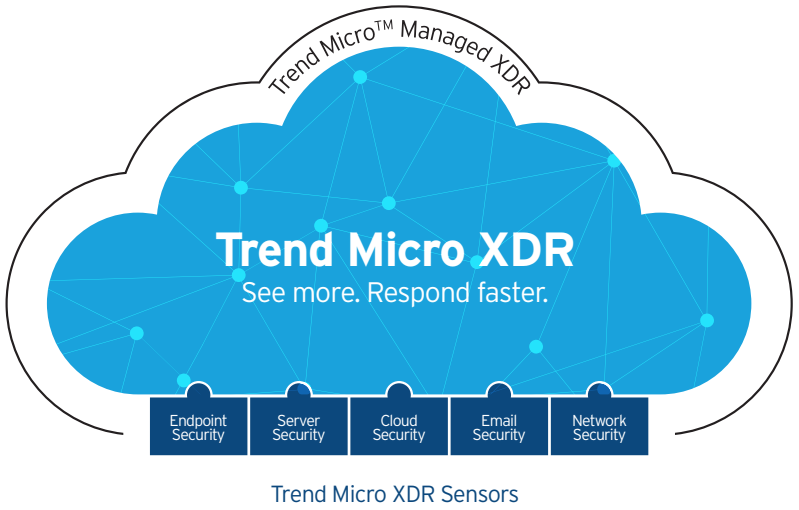
Trend Micro XDR delivers extended detection and response for email, endpoints, servers, cloud workloads, and networks. It offers broader visibility and expert security analytics leading to fewer alerts and higher-confidence detections for earlier, faster response. With XDR, customers can identify and respond more effectively and efficiently to threats, minimizing the severity and scope of an attack on the organization. XDR for Networks is a valuable part of the Trend Micro XDR solution, providing critical logs and visibility into unmanaged systems such as; contractor/third-party systems, Internet of Things (IoT) and Industrial Internet of Things (IIoT) devices, printers, and bring-your-own-device (BYOD) systems.
Features
Visualize the attack
Trend Micro Deep Discovery Inspector includes XDR capabilities to correlate detection events showing you:
- What the first point of attack was
- Who else in the organization is impacted
- Where the threat is calling out to
- How the initial breach happened*
- Others who may also be a target**
Standards-based sharing
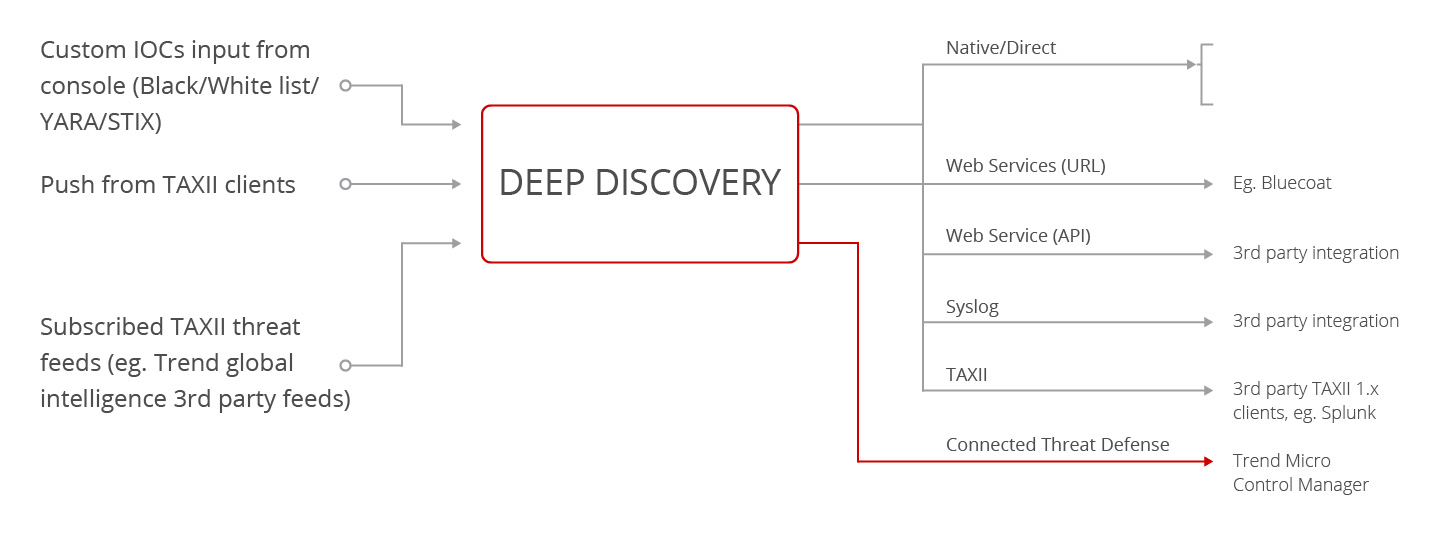
Collect advanced threat intelligence from TAXII feeds or clients along with customer indicators of compromise (IoC) inputs, and share threat intelligence across your network, so you can stop worrying about missing new threats.
Event correlation
Examines the relationship between events to help you understand the full extent of the attack, including both high and low severity events, allowing you to block all aspects of future attacks.
Prioritize and simplify attack data
Detecting, alerting, and blocking threats can produce a glut of data. To assist security professionals in the time-consuming task of combing through potentially thousands of alerts or logs, Deep Discovery Inspector with XDR correlates all the events to show what the first point of entry was by identifying patient zero, who else has been breached, so you can see the full scope of the attack, where the threat is calling out to, how the threat made its original infection,* and others who may also be a target.**
Detect threats faster with advanced sharing
Staying ahead of the threat landscape is difficult, especially when you are managing multiple security solutions. Deep Discovery ingests the latest advanced threat intelligence, or IoCs, from threat feeds and custom inputs (STIX/TAXII and YARA) and shares the IoCs with Trend Micro and third-party solutions.
This enables all the connected products to detect and block the previous unknown threats, giving your security operations center (SOC) greater visibility and control against attacks.
Get real-time visualization of targeted attacks
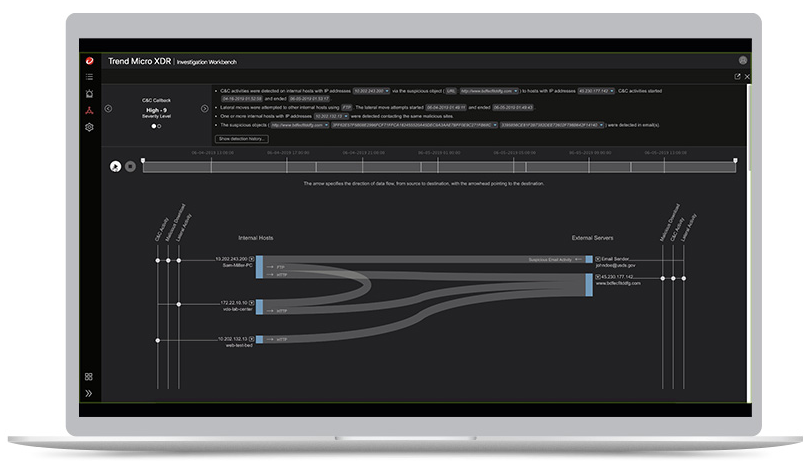
In some cases, you may think the attack started today, but, in fact, the breach happened weeks ago. An easy-to-read Sankey diagram lets you see every step of the attack, dating back six months. Deep Discovery Inspector with XDR extracts metadata from the network traffic and correlates the events in a graph for real-time visibility. You get faster resolution with fewer people involved and a bigger picture of the full attack.
*requires Trend Micro Apex One as a Service with XDR
**requires Trend Micro Cloud App Security with XDR
Capabilities
See the full attack lifecycle
An attack isn’t just a point in time. Advanced or targeted attacks take time and use multiple attack vectors to execute. XDR for Networks gives you the chronological order of correlated threat events to easily visualize the entire life cycle and truly understand the attack and protect yourself from future attacks.
Full visibility into the “what”, “who”, and “where”
XDR for Networks will correlate and help simplify threat events to show you: What was the first point of entry of the attack? Who else in the organization has been impacted by the attack? Where was the threat calling out to? (i.e. command and control (C&C) communication). With visibility and answers into these three questions, you will have a better understanding of the threat’s impact on your organization and how to prioritize your response.
Get greater context for greater understanding
XDR collects and correlates deep activity data for one or more vectors—email, endpoints, servers, cloud workloads, and networks—enabling a level of hunting and investigation analysis that is difficult or impossible to achieve otherwise.
Prioritize your response
By knowing the extent of an attack and its severity you can determine which threat requires immediate response and which threats may be able to wait.
Play out the attack
With the click of a button you can see the entire attack play out chronologically from the URL redirects, to the initial infection point, to the lateral spread across the network. See every movement or scale it down to just view what happened this morning or over a weekend.
Dig deeper into each step of the attack quickly
It is great to have visibility into an attack but sometimes you need the details. Just by hovering your mouse over an attack event, you can immediately see pertinent details of the attack at network and endpoint event levels such as; protocol used, severity, triggered rule, SHA1, number of transactions and dates they span, etc.
Correlate retroactively against historical network data
The average threat can go undetected for over three months once it slips past your existing security. In most cases, when you finally see it you may never know when it first entered your network or how. By storing the events for six months or more you can look back at delayed attacks and see not only how it spread, but also the infection point to make sure you put the right safeguards in place so it doesn’t happen again.
Flexible deployment options
Prefer to keep everything in-house? Want to offload everything to the cloud? Choose the deployment option to meet your needs, offered as an on-premises solution (Deep Discovery Network Analytics) or an “asa-service” solution (XDR for Networks) hosted in the cloud. If you keep it on-premises you will benefit from integration with the endpoint (Trend Micro Apex One™) to add more context around each attack. For full XDR, the as-a-service solution will provide broader visibility across endpoints, servers, cloud workloads, and email.
System Requirements
Integrated products
- Trend Micro Deep Discovery Director 3.0 or later
- Trend Micro Deep Discovery Inspector 5.1 or later
Virtual appliance
- Virtual machine with the following minimum specifications:
- Hypervisor: VMware® vSphere ESXi 6.5, Microsoft® Hyper-V® in Windows® Server 2016
- Deep Discovery Director Network Analytics is an appliance based on CentOS Linux® 7 (64-bit)
- Network interface card: 1 with 1 Gbps adapter
- SCSI controller: LSI Logic Parallel
- CPU: 1.8 GHz (8-12 cores)
- Memory: 64 GB
- Hard disk: 6 TB (thick provisioned)
| |
XDR add-on: Trend Micro Deep Discovery Inspector |
Deep Discovery Network Analytics on-premises |
Deep Discovery Network Analytics 9000 Series appliance |
| Combined Deep Discovery Inspector throughput |
1Gbps – 20Gbps |
1Gbps – 4Gbps |
5Gbps – 10Gbps |
| Form factor |
SaaS |
Requires on-prem storage (~2.3 TB per Gbps) |
1U Rack-Mount, 48.26 cm (19”) |
| Event data retention |
Up to 180 Days |
Up to 180 Days |
Up to 180 Days |
| Prerequisite solution |
Trend Micro Deep Discover Director 5.3 or later (virtual appliance) optional |
Deep Discovery Director 5.8 or later (virtual appliance) |
None |
| Dimensions (WxDxH) |
N/A |
N/A |
43.4 (17.08") x 72.8 (28.68") x 4.28 (1.69") cm |
| Weight |
N/A |
N/A |
17.5kg (38.58 lb) |
| Data Ports |
N/A |
N/A |
10/100/1000 BASE-T RJ x 1 |
| AC Input Voltage |
N/A |
N/A |
100 to 240 VAC |
| AC Input Current |
N/A |
N/A |
7.4A to 3.7A |
| Hard Drives |
N/A |
N/A |
7 x 1.92TB |
| RAID Configuration |
N/A |
N/A |
RAID 5 |
| Power Supply |
N/A |
N/A |
550W Redundant |
| Power Consumption (Max) |
N/A |
N/A |
604W |
| Heat |
N/A |
N/A |
2559 BTU/hr (Max.) |
| Frequency |
N/A |
N/A |
50/60 Hz |
| Operating Temp |
N/A |
N/A |
10 to 35 °C (50-95 °F) |
| Hardware Warranty |
N/A |
N/A |
3 Years (extendable to 5 years) |
With this configuration and a typical enterprise level of network traffic, Deep Discovery Director Network Analytics can service:
| Deep Discovery Network Analytics |
XDR add-on: Deep Discovery Inspector |
Up to 4 Gbps of combined Trend Micro Deep Discovery Inspector throughput
Eg. 1 DDI 4000 or 4 DDI 1000 |
Up to 20 Gbps of combined Deep Discovery Inspector throughput
Eg 2 DDI 9000 or 5 DDI 4000 |
Management console
- Google Chrome latest version
- Mozilla Firefox latest version
- Microsoft Internet Explorer latest version
- Recommended resolution: 1,280x800 or higher