Trend Micro TXOne StellarProtect
Industrial-grade, next-generation endpoint security for ICS

First-of-a-kind all-terrain endpoint protection for ICS devices
Overview
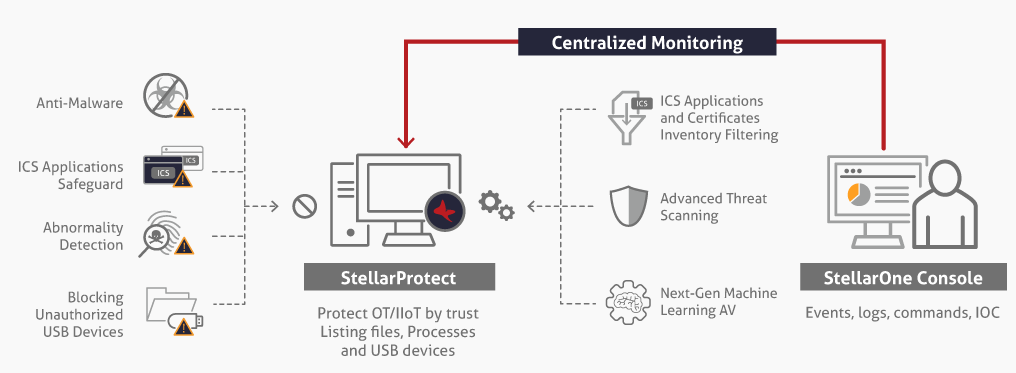
Securing ICS endpoints introduces difficulties for both operational engineers and security administrators. Though traditional antivirus has long been seen as a core part of cyber defense strategy, the test of time has shown it brings shortcomings to work sites. All antivirus software requires constant virus signature updates over the Internet to be able to scan for threats. These scans, in turn, place heavy demand on both CPU loading and memory consumption as intensive I/O hooking is conducted. This puts availability at risk even in work sites running modernized operational devices. Safeguarding ICS endpoints requires different priorities: chosen solutions must ensure daily working processes are never jeopardized, computation is never slowed, and production decisions are never delayed. TXOne StellarProtect is the first solution of its kind: all-terrain endpoint protection, a defensive solution custom-engineered for operational technology. Its advanced threat scanning brings known attacks to heel while its next-gen machine learning engine blocks unknown threats, requiring no internet access. StellarProtect’s ICS filtering, based on an inventory of applications and certificates, eliminates unnecessary overhead to allow the most lightweight operation possible. Effective in a range of environmental conditions with high accuracy and very low impact on endpoint performance, StellarProtect provides full coverage in one deployment.
Purpose-built for ICS
StellarProtect delivers patternless protection against both known and unknown malware via machine learning and ICS root of trust. ICS root of trust collects over a thousand ICS software certificates and licenses, verifying them in advance to reduce protection overhead.
All-terrain protection
ICS endpoints often operate in a harsh environment, where they must output consistent and uninterrupted performance. StellarProtect can operate without an internet connection, using policies designed around “least privilege” to thwart both known and unknown malware as well as fileless attacks.
Zero trust operation
StellarProtect continuously monitors the system to learn how users interact with ICS applications. With this information, it automatically determines whether an application can be trusted with access to files, the system library, or registry keys.
Agent
- Real-time malware protection
- Ransomware and fileless attack prevention
- Advanced threat protection
- Exploit prevention
- Behavior anomaly detection
- IOC integration
- USB device trust listing
- ICS application inventory informed by OT vendors
- Write-protection
- Support for both scheduled and on-demand AV scans
- Log aggregation
Management Console (StellarOne)
- Centralized monitoring
- Notifications designed to minimize alert fatigue
- Account management
- Syslog forwarding
- Trusted certificate management
- Support for IOC integration
- Integrate MITRE ICS IDs in event logs
- Scan exclusion management