Overview
The data center is undergoing a tremendous transformation. Organizations are now moving their server workloads to the cloud, and even leveraging containers and serverless in their cloud-native application architectures. There are many advantages of hybrid cloud computing, however, it also comes with new risks and threats. Your organization must ensure compliance requirements are met, and that you have unified security across all of your workloads such as physical servers, virtual, cloud, or containers.
Trend Micro Cloud One – Workload Security provides comprehensive detection and protection in a single solution that is purpose-built for server, cloud, and container environments. Workload Security allows for consistent security, regardless of the workload. It also provides a rich set of application programming interfaces (APIs), so security can be automated and won’t impact your teams.
Automated
Security as code lets your DevOps teams bake security into their build pipeline to release continuously and frequently. With built-in automation, including automated discovery and deployment, quick-start templates, and our Automation Center, secure your environment and meet compliance requirements quickly.
Flexible
Builder’s choice. Security for your hybrid cloud, multi-cloud, and multiservice environments, as well as protection for any vintage of application delivery—all with broad platform support.
Better Together
Adopt the Trend Micro Cloud One – Endpoint Security service alongside Workload Security to protect user endpoints, servers and cloud workloads using a single platform, and with unified management and role-based access control. Eliminates the cost and complexity of deploying multiple point solutions while achieving specialized security optimized for your diverse endpoints and workloads.
Key Business Issues
- Automated protection
Save time and resources with automated security policies, deployments, health checks, and compliance reporting across your hybrid environments, such as data center and cloud, as you migrate or create new workloads.
- Complete security
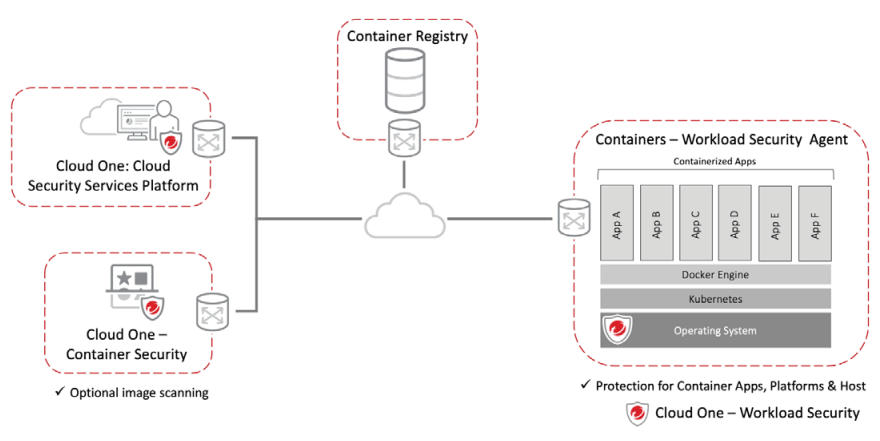
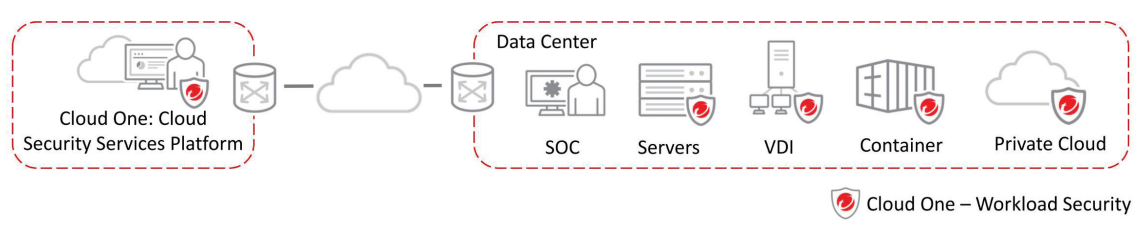
Deploy and consolidate detection and protection across your physical, virtual, multi-cloud, container, and user endpoint environments with a single agent.
- Security for the CI/CD pipeline
API-first, developer-friendly tools to help you ensure that security controls are baked into DevOps processes.
- Accelerated compliance
Demonstrate compliance with several regulatory requirements, including GDPR, PCI DSS, HIPAA, NIST, FedRAMP, and more.
Detection and Protection Capabilities
Network security tools detect and stop network attacks to protect vulnerable applications and servers
- Host-Based Intrusion Prevention: Detects and blocks network-based exploits of known vulnerabilities in popular applications and operating systems using IPS rules.
- Firewall: Host-based firewall protects endpoints on the network using stateful inspection.
- Vulnerability Scanning: Performs a scan for known network-based vulnerabilities in the operating system and applications.
System security tools lock down systems and detect suspicious activity
- Application Control: Blocks any executables and scripts that aren’t identified as known-good applications or DLLs from installing/ executing.
- Log Inspection: Identifies and alerts unplanned changes, intrusions, or advanced malware attacks, including ransomware as it is happening on your systems.
- File Integrity Monitoring: Monitors files, libraries, and services, etc, for changes. To monitor a secure configuration, a baseline is created that represents the secure configuration. When changes from this desired state are detected, details are logged and alerts can be issued to stakeholders.
Malware prevention stops malware and targeted attacks
- Anti-Malware:
i. File Reputation: blocks known-bad files using our anti-malware signatures.
ii. Variant Protection: looks for obscure, polymorphic, or variants of malware by using fragments of previously seen malware and detection algorithms.
- Behavioral Analysis: Examines an unknown item as it loads and looks for suspicious behavior in the operating system, applications, and scripts, as well as how they interact, to block them.
- Machine Learning: Analyzes unknown files and zero-day threats using machine learning algorithms to determine if the file is malicious.
- Web Reputation: Blocks known bad URLs and websites.
- SAP Scanner*: Enables anti-malware scanning for Netweaver through the SAP Virus Scan Interface (VSI).
- TLS Inspection: Inspects SSL/TLS content for threats and prevents attacks without having to manage keys and certificates, increasing security posture, and providing better protection.
*The SAP Scanner requires specialized functionality that must be purchased separately from your Workload Security license.
System Requirements
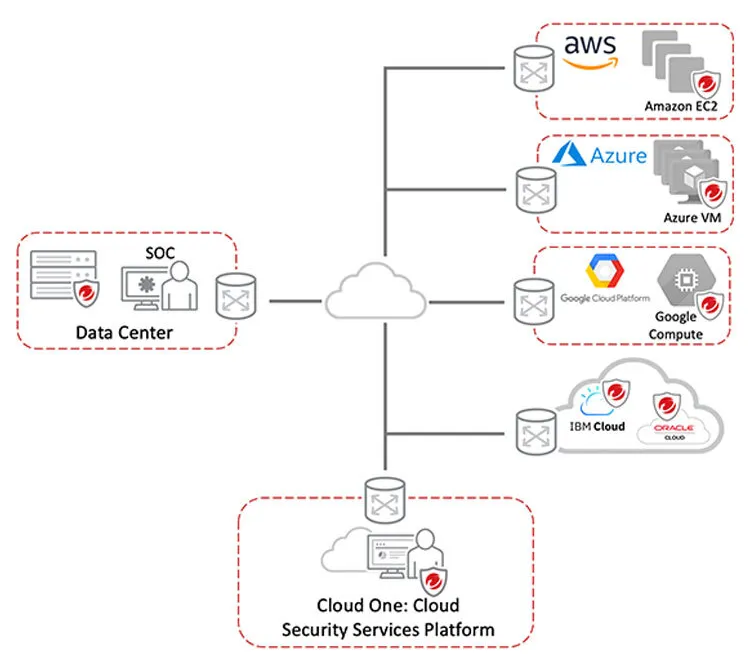
Workload Security is software as a service (SaaS) hosted by Trend Micro in the cloud, which means additional value from new capabilities and security functionality are delivered continuously. We manage regular product and kernel updates, set up and maintain the security database, and administer the management platform. Our cloud-based security offering enables quick setup, local and regional flexibility as well as automates and simplifies security operations for cloud instances.
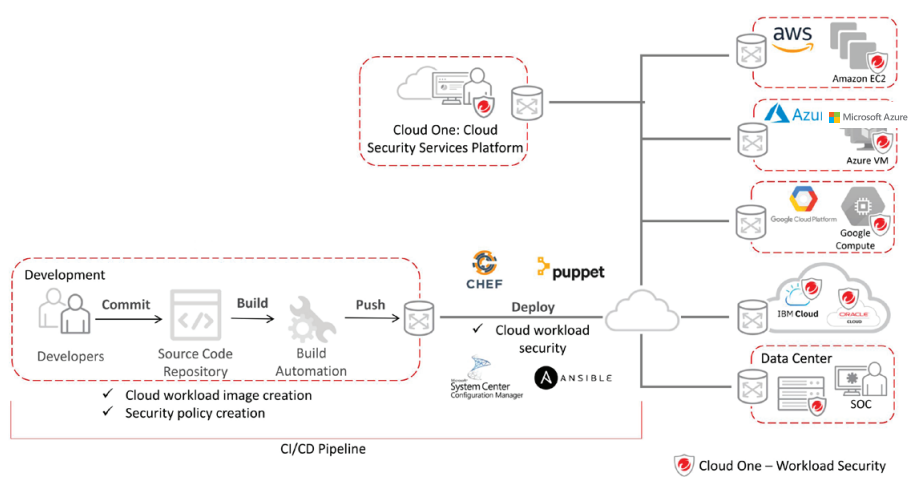
Workload Security Agent enforces the platform’s detection and protection policy (application control, anti-malware, IPS, firewall, integrity monitoring, and log inspection) via a small software component deployed on the endpoint, server, or VM being protected. This can be automatically deployed with leading operational management tools like Chef, Puppet, Ansible, Microsoft System Center Configuration Manager, and AWS OpsWorks.
System Requirements
- Workload Security is available as a service, and all management components are hosted and maintained by Trend Micro
Supported Platforms (For Agent)
- Trend Micro constantly supports new operating systems and versions, including Microsoft Window, Linux, Solaris, AIX, and Docker containers
- Workload Security is also available as a software to run in your data center or cloud
Built for Security in the Cloud
Workload Security is optimized for leading cloud providers’ infrastructures, including support for many operating systems, examples include:

Compatibility with configuration, event, and orchestration tools:

Key Certifications, Compliance, and Alliances

- AWS Advanced Technology Partner
- AWS Container Competency Partner
- ISO 27001/ISO 27014/ISO 27017
- PCI DSS
- GDPR
- HP Business Partnership
- Microsoft Certified Partnership
- SOC 2
- Virtualization by VMware
- VMware Cloud on AWS Partner
- VMware Global Partner of the Year
- Microsoft Application Development Gold Partner