
Trend Micro Zero Trust Secure Access
Redefine trust and secure digital transformation with continuous risk assessments
Redefine trust and secure digital transformation with continuous risk assessments
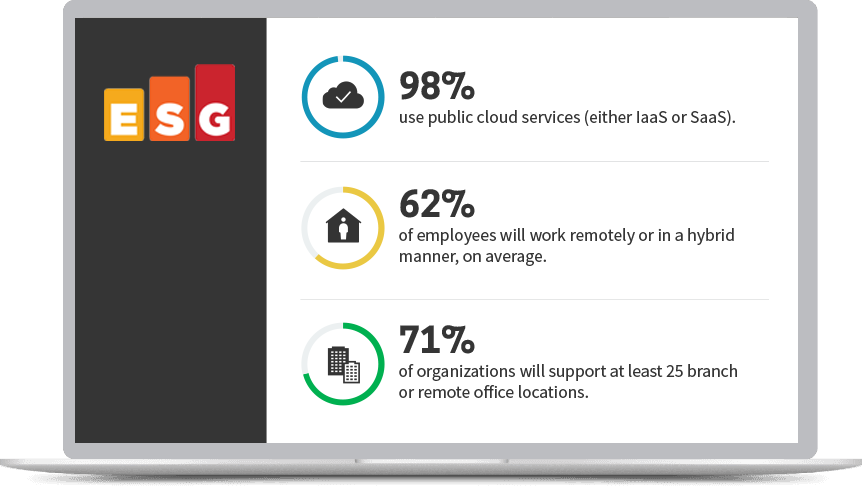
As the recent transition to a remote or hybrid workforce has widened the digital attack surface, increasing cyber risk significantly across many organizations, the old adage of “trust, but verify” is no longer practical. The growing interest and movement toward Zero Trust architectures in the past few years has shifted this approach to the more accurate, “never trust, always verify”.
And for good reason. The broad implicit-trust methods and practices haven’t kept pace with stealthy, more resourceful threat actors. Organizations need to modernize the methods used to securely connect users, devices, and applications no matter where they are or what they need to access.
How Application Security Works
In most organizations, implicit trust is the standard. This opens the organization to considerable risk, where a single compromised identity can begin to wreak havoc in the environment and largely move throughout the network unabated.
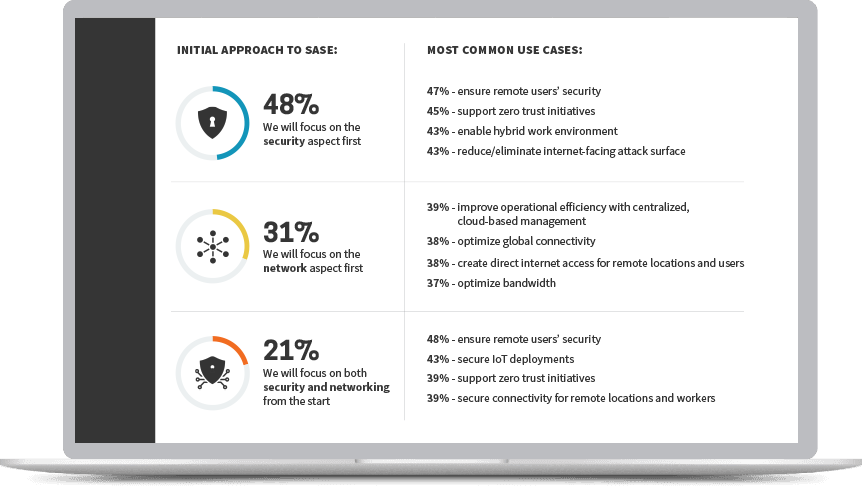
Much like digital transformation, the path toward Zero Trust is a journey, not a solution. There are a number of ‘initial steps’ that can be taken depending on the highest priority risk in your organization and your current security posture. While more use cases exist, which over time can be implemented as your organization moves towards Zero Trust architecture, the initial steps include:
- Securing access to the internet
- Delivering fast and secure access to cloud applications
- Transforming your remote access solution
Introducing Trend Micro Zero Trust Secure Access
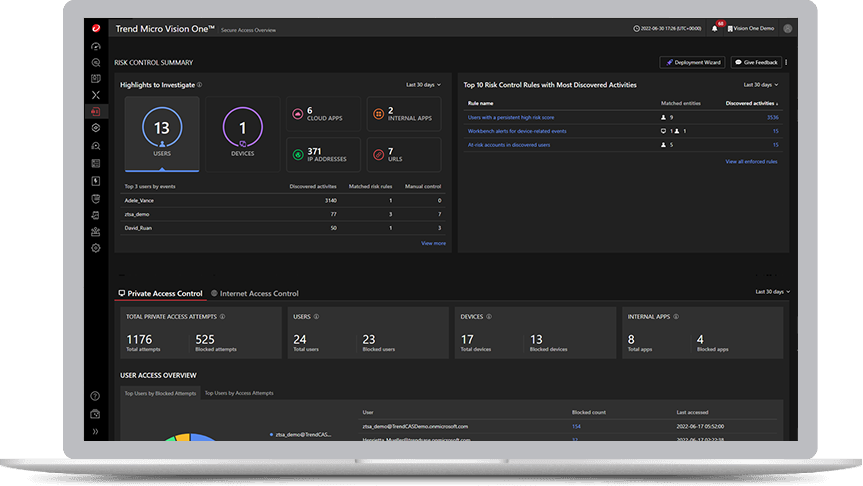
As part of Trend Micro Vision One, Trend Micro Zero Trust Secure Access follows the principles of Zero Trust networking. This strengthens your overall security posture by enforcing strong access control permissions from multiple identity services across the organization.
Instead of granting access to the entire network, as a VPN does, Zero Trust Secure Access provides a gateway to specific applications and resources, restricting access to everything within the network that is not being employed. If valid user credentials are stolen, the level of access they will grant to the organization can be contained, effectively reducing the blast area of any attack.
Secure access to the internet
More than ever, businesses run on SaaS apps accessed over the internet.
- Gain visibility into the sensitive data processed and stored in these apps
- Introduce trust-based access for sanctioned and unsanctioned apps
- Leverage simple control with a unified policy
Deliver fast, protected access to cloud applications
Digital transformation includes migrating apps to public clouds.
- Reduce the risk of unauthorized access
- Increase performance of SaaS and business applications and organizational resources
- Remain secure with continuous risk assessment
Transform your remote access solution
The work from anywhere movement has become a reality for many organizations.
- Securely connect your virtual workforce to individual corporate resources
- Retire legacy VPN and bulky virtual desktop solutions
- Introduce high-performance just-in-time access control
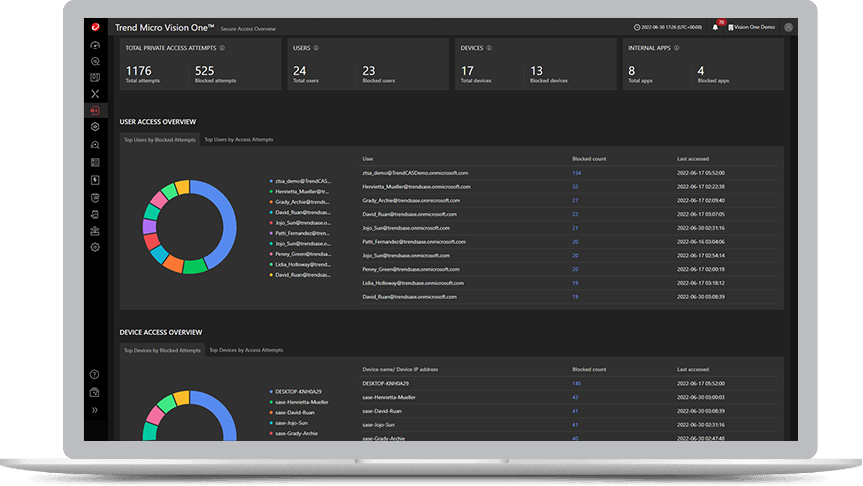
Continuous risk assessment
Single point-in-time assessment of an asset’s risk gives a false sense of security. Trend Micro Zero Trust Secure Access implements continuous risk assessment by analyzing threat factors of assets. Access to specific resources can be changed dynamically based on increases or decreases in risk. Trend Micro Vision One Risk Insights gathers telemetry and data to automate decisions by leveraging the Trend Micro endpoint agent and network tools.
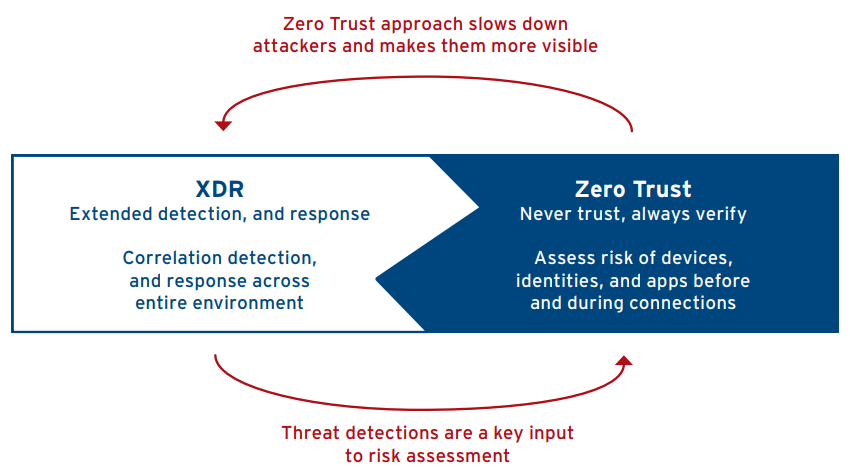
A native part of your XDR strategy
Connecting email, endpoints, servers, cloud workloads, and networks provides a broader perspective and a better context to hunt, detect, and contain threats.
