Overview
Trend Micro TippingPoint Security Management System (SMS) provides a scalable, policy-based operational model and enables straightforward management of largescale Trend Micro TippingPoint deployments.
TippingPoint SMS enables:
- Big-picture analysis with trending reports
- Correlation and real-time graphs on traffic statistics
- Filtered attacks
- Network hosts and services
- Inventory and health status for TippingPoint devices
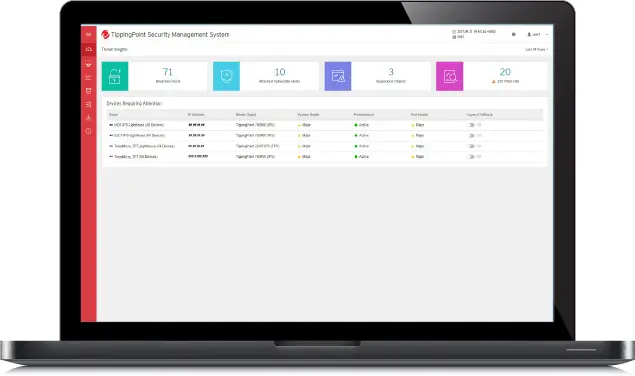
A significant component of TippingPoint SMS is the dashboard. It provides at-aglance monitoring and launch capabilities into targeted management applications. It also presents an overview of current performance for all TippingPoint devices in the network, including notifications of updates and potential issues that may need attention. Customers can customize the TippingPoint SMS dashboard to their specific needs by using a dashboard palette of drag-and-drop configurable gadgets that are categorized by health and task status, inspection event, event rate, security, reputation, application, and user.
TippingPoint SMS Dashboard
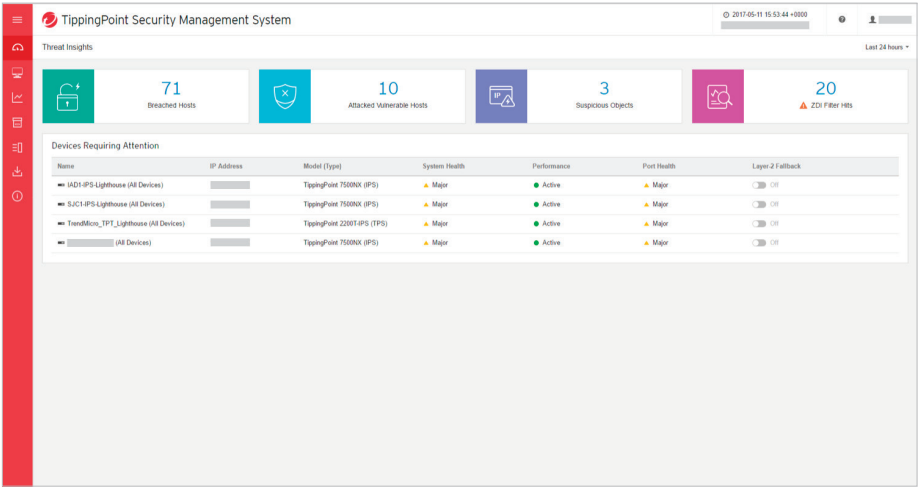
Threat Visibility and Prioritization
SMS Threat Insights is an aggregation portal that takes events from TippingPoint devices, vulnerability scanners, and sandboxing solutions, and displays them in one place to prioritize, automate, and consolidate network threat information.
This allows multiple security groups to have a common framework for discussion and resolution. By correlating and automating threat data from multiple security tools, SMS Threat Insights assist security professionals by prioritizing incident response measures for breaches or potential vulnerabilities. The portal provides views and actionable data on:
- Breached hosts
Information is correlated from TippingPoint and Trend Micro Deep Discovery Analyzer (sandbox) to help prioritize events for response. Security professionals can isolate, seek out, and quarantine users on the network who appear to be infected or acting suspiciously.
- Attacked vulnerable hosts
Integrated with third-party vulnerability scanners (Rapid7, Tenable, and Qualys) to prioritize Trend Micro DV filters based on actual vulnerabilities in a unique environment. This gives users the ability to quickly enable filters in which they may have been previously unaware.
- Suspicious objects
Incident response is integrated between Trend Micro Deep Discovery and TippingPoint via the SMS. By automatically submitting identified potential threats (like URLs) from TippingPoint to the Deep Discovery sandbox, it isolates and investigates the risk, converting unknown, potential threats into known threats. These suspicious objects can then be viewed in SMS Threat Insights to ensure that users are protected.
- Trend Micro Zero Day Initiative (ZDI) filter hits
Undisclosed threats are vulnerabilities that are unknown to the public—outside of Trend Micro and the impacted software vendor—that could potentially be zero-day threats. The Trend Micro Forward-Looking Threat Research (FTR) team, in collaboration with ZDI, provides preemptive protection from undisclosed and zero-day threats through exclusive access to vulnerability information. In most cases, this preemptive protection is available before a vulnerability is disclosed or exploited. SMS Threat Insights display filters that trigger on the potentially most impactful threats to give security response teams visibility into the high-priority, undisclosed zero-day filters protecting vulnerabilities in their environment and help prioritize events that may require immediate action.
Features
Actionable Threat Intelligence
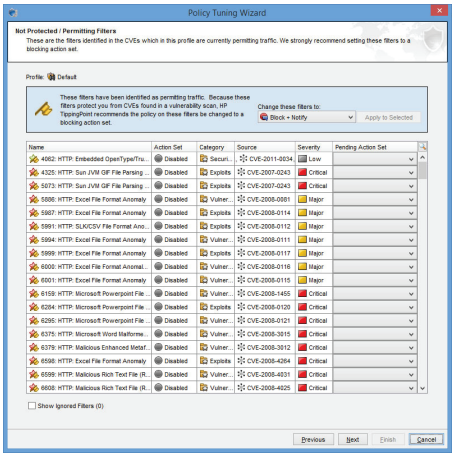
The TippingPoint Security Management System (SMS) provides global vision and security policy control for threat intelligence and enables comprehensive analysis and correlation. You can configure it to automatically check for, download, and distribute filter updates to TippingPoint systems as well as to take immediate action on events based on your security policies.
- Operationalizes machine-readable threat intelligence (MRTI) through support for STIX and TAXII information sharing
- Consumes threat intelligence feeds from third party sources via APIs
Enterprise Vulnerability Remediation (eVR)
Map vulnerabilities to Trend Micro threat intelligence, take immediate action to maximize security coverage, and remediate through vulnerability threat prioritization.
- Quickly optimize your network security with virtual patches for active CVEs in your network
- Simplify policy decisions based on latest threat intelligence>
- Enhance and improve compliance processes
Advanced Threat Analysis
TippingPoint solutions automatically block known and undisclosed vulnerabilities from the network. Added forensic capabilities automatically forward unknown or suspicious indicators of compromise (IOCs) to Deep Discovery for in-depth sandbox analysis and remediation, all without changing policy or altering network infrastructure.
Contextual Awareness
SMS provides contextual and end-user awareness on security and threats. Security policies can be defined and easily changed to fit the rhythm of business operations and respond to threats as they arise.
- Detects and blocks network traffic based on a geographic region or country
- Integrates with Active Directory (AD) to provide context, visibility, and reporting of compromised users by mapping IP addresses to AD users, machines, domains, and AD groups
Threat Insights
Gain visibility into the volume and severity of threats attacking your network. Threat Insights aggregates and collects threat data from TippingPoint, Deep Discovery, and third-party solutions to give you visibility into which attacks require immediate response and which ones were thwarted, allowing you to prioritize, automate, and integrate network threat information.
Proactive Response and Remediation
Through an automated response system called Active Responder, you can specify an action in response to a security event, ranging from directing a user to a self-remediation site, generating a trouble ticket, or – if the event is severe enough–moving to a secure VLAN or removal from the network.
GEO/Location Filtering
TippingPoint SMS can be configured to detect and block network traffic based on a computer’s IP address and host name within a geographic region or country. Customers can establish an action set associated with geographic filters to minimize or eliminate communications with potentially risky systems.
Microsoft Active Directory (AD) Integration
TippingPoint SMS can provide visibility, enhanced context, and reporting on the traffic of a particular user through AD integration. The username, domain, machine, and user group are all tracked and available for forensics, reporting, and filtering results (for example, see all attacks targeted to machine X or from user Y). Administrators can also see the IP history of a particular AD user or the user history for a particular IP.
Comprehensive Network Traffic Visualization
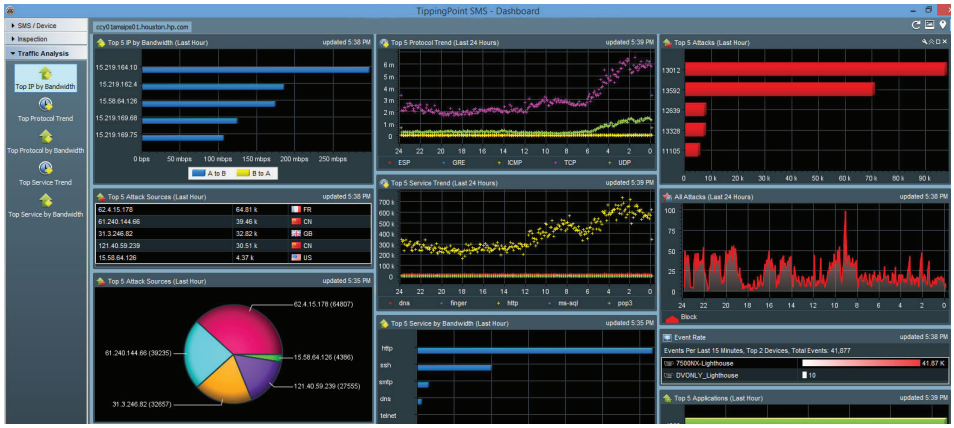
TippingPoint solutions can support the export of network flow data statistics for visualization and analysis. With TippingPoint SMS, statistics and flow data summaries can be viewed and analyzed to optimize performance and help identify compromised hosts as well as other suspicious and malicious network traffic.
Device Configuration and Monitoring
TippingPoint SMS management can scale up to hundreds of devices or drill down deep into the internal workings of TippingPoint devices. In addition, a single client can operate across multiple TippingPoint SMSes for even greater scalability. Network parameters, as well as TippingPoint device and filter behaviors, can be viewed, assessed, and tuned from one interface.
Third-Party Integration
SMS integrates seamlessly with other Trend Micro solutions, as well as with SIEM, vulnerability management tools, and other complementary security solutions. Gain centralized visibility into your network to make informed decisions and take immediate action on any potential threats to infrastructure or data.