Trend Micro TXOne StellarEnforce
System lockdown software for mission-critical devices

Protect your ICS environments with industrial-grade system lockdown security
Overview
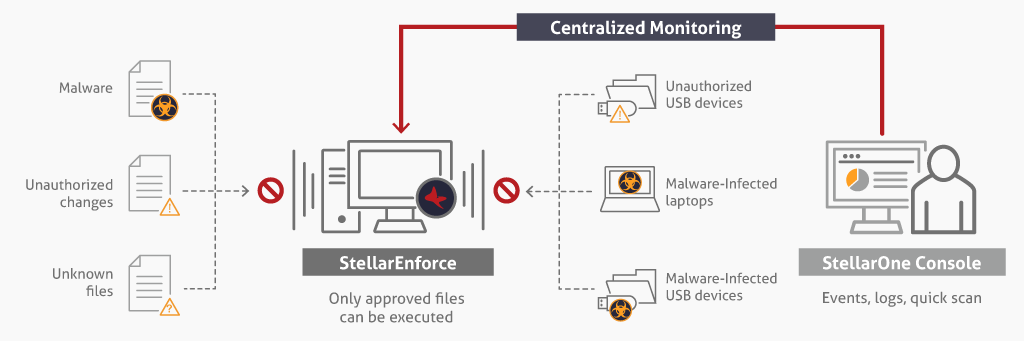
Organizations today such as factories, health care centers, and utility companies are facing a growing number of cyber threats. Industrial control systems (ICS), industrial IoT assets, and the embedded devices essential to daily operations are all facing rapidly-increasing risk. Critical assets relying on older operating systems are especially vulnerable as they are likely difficult or impossible to patch, running with vulnerabilities attackers can easily exploit. TXOne StellarEnforce locks down sensitive assets, limits access, and preserves system resources with its simple and reliable trust list technology. Once deployed, this solution only allows the execution of approved applications necessary to daily operations, preventing the spread and execution of malware without reliance on pattern files or other resources.
Streamlined trust listing
With trust listing only pre-registered applications and services can run, so that mission-critical systems are protected from malware with minimal impact on performance. Unlike traditional cybersecurity software, StellarEnforce requires no internet connection, no periodic updates, and no regular malware scans.
4-in-1 lockdown confirmation
TXOne StellarEnforce secures operational integrity with 4-in-1 lockdown confirmation: operation lockdown, USB device lockdown, data lockdown, and configuration lockdown, efficiently reducing the chance of downtime and cost of resilience.
Legacy assets protection
Because StellarEnforce requires no regular updates and supports a variety of Microsoft operating systems past their end-of-service date (Windows 2000, Windows XP, and more), it doesn’t affect operating performance.
Agent
- Application trust listing
- USB device trust listing
- Maintenance mode
- Write protection
- Integrity monitoring
- File-less attack prevention
- Exploit protection
- Trust list management
- Pre-scan (malware inspection during install)
- Role-based administration
- Support for both scheduled and on-demand AV scans (StellarEnforce AV Edition)
- Log aggregation
- Intelligent runtime learning
Management Console (StellarOne)
- Centralized monitoring
- Notifications designed to minimize alert fatigue
- Account management
- Syslog forwarding
- Trusted certificate management
- Support for IOC integration
- Integrate MITRE ICS IDs in event logs
- Scan exclusion management